[NEWS] Azure News of the week
5. Juli 2024Also this week there were many news around Microsoft Azure! Here as always the overview for you: Have fun reading and trying it out… Dieser Post ist auch verfügbar auf: Englisch
As we figured out last week, Azure Role-Based Access Control (RBAC) is a very important thing, when it comes to the Management of Microsoft Azure. But there is another important feature you should know to keep control: Azure Policy
Remember the function of RBAC, where Security Principal, Role and Scope meet each other and define you final set of rights:
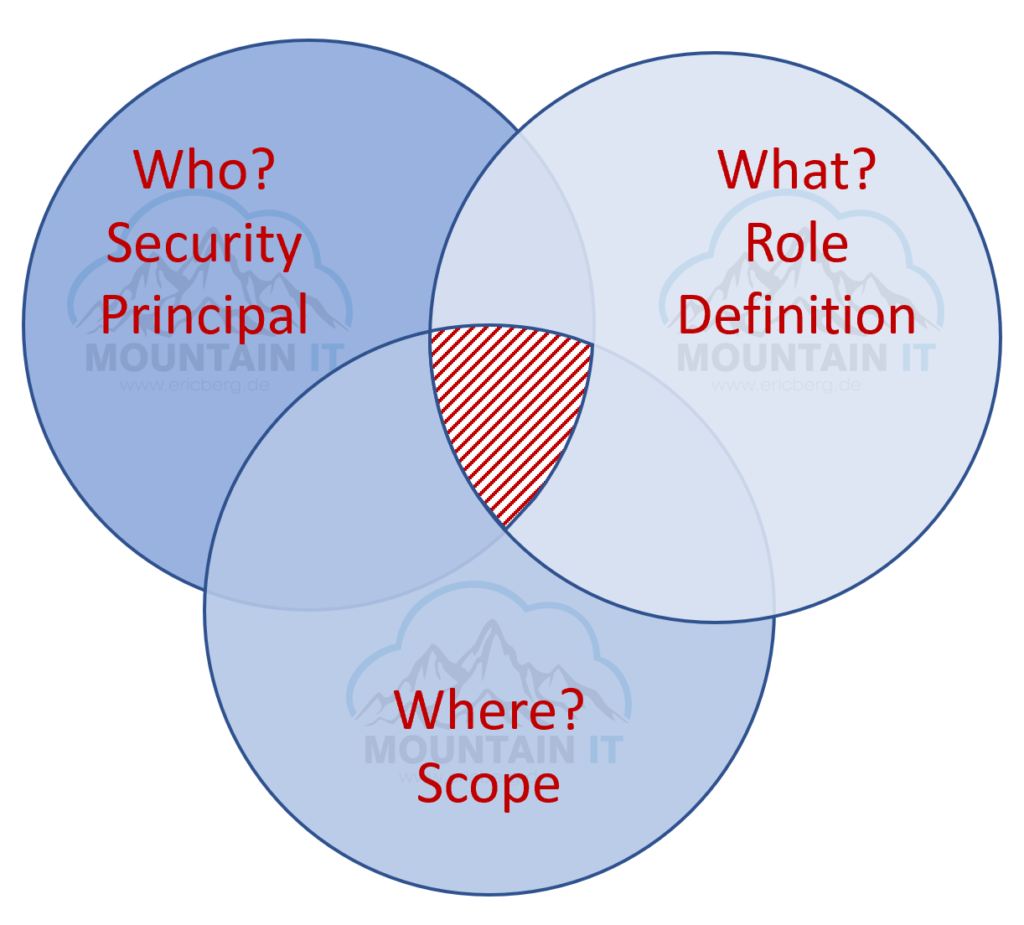
If you think about this, you will figure out that you still may have an issue. If a user has the right to create VMs … he can create any VM he wants, in any region he wants. And as we know, VMs in Azure can cost 80$ a month or for the larger sizes go up to 200.000$ a month. So you may wish to have a solution for this.
Another problem is that you can control what a user can do, but not really how a resource looks like. So people with the right role can create Storage accounts, but nobody is forcing to set https as required. Admins with the respective role can create VMs but they may forget to add a backup. Also you cannot define how the „inside-configuration“ of a VM looks like. Network Admins may create a Public IP, but assign it to internal systems by accident.
These are things you cannot solve with roles, scopes or security principals … this is the moment when you start to love Azure Policy capabilities…
Azure policy is the default allow and explicit deny system in Azure. It focuses on the resource properties of a resource, like:
So it is the perfect addition to RBAC … as RBAC gives you explicit access … Policy defines the configurations you can to and which one are not allowed.
So very common Policies are:
If you want to manage your Azure Policies you can do this via the Azure Portal, via CLI or PowerShell or even via CI/CD or Blueprints. So you can see there are multiple options. As this is a basic article, let’s try the easy way through the portal.
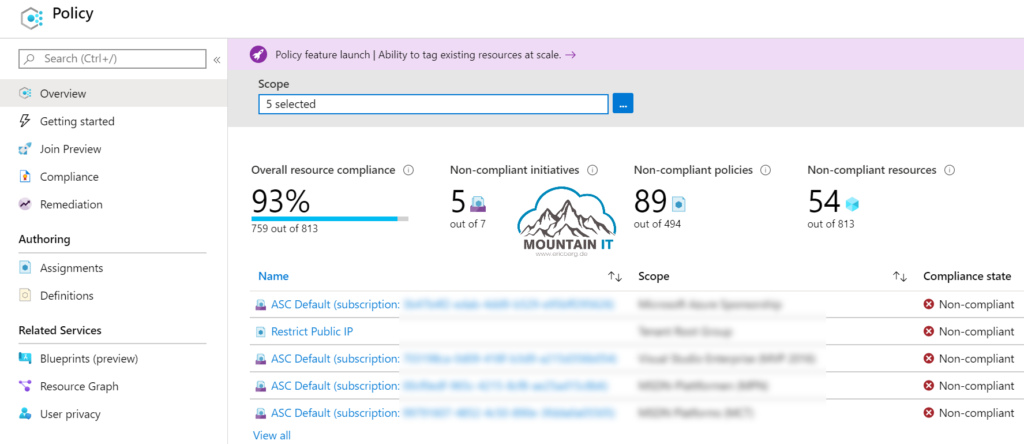
You can find the „Policy“ view in the Azure Portal. Here you can see a compliance overview across all your subscriptions and resources. There are some default policies like the „ASC Default“ which are set by and for Azure Security Center.
Azure Policy works with Definitions and Assignments. Definitions can be grouped together to Initiatives. To make it simple:
Policy Definition work with an if-then approach and look like:
{
"properties": {
"displayName": "Restrict Public IP",
"policyType": "Custom",
"mode": "All",
"metadata": {
"category": "Network"
},
"parameters": {},
"policyRule": {
"if": {
"allOf": [
{
"field": "type",
"equals": "Microsoft.Network/publicIPAddresses"
},
{
"field": "location",
"equals": "westeurope"
}
]
},
"then": {
"effect": "deny"
}
}
},
[...]
}There are hundreds of pre-defined policies in Azure, but you can always choose to create your own policy.
If you want to learn more about Azure Policy have a look into the following resources:
Happy policying 😉
Dieser Post ist auch verfügbar auf:
 Englisch
Englisch
Leave a comment